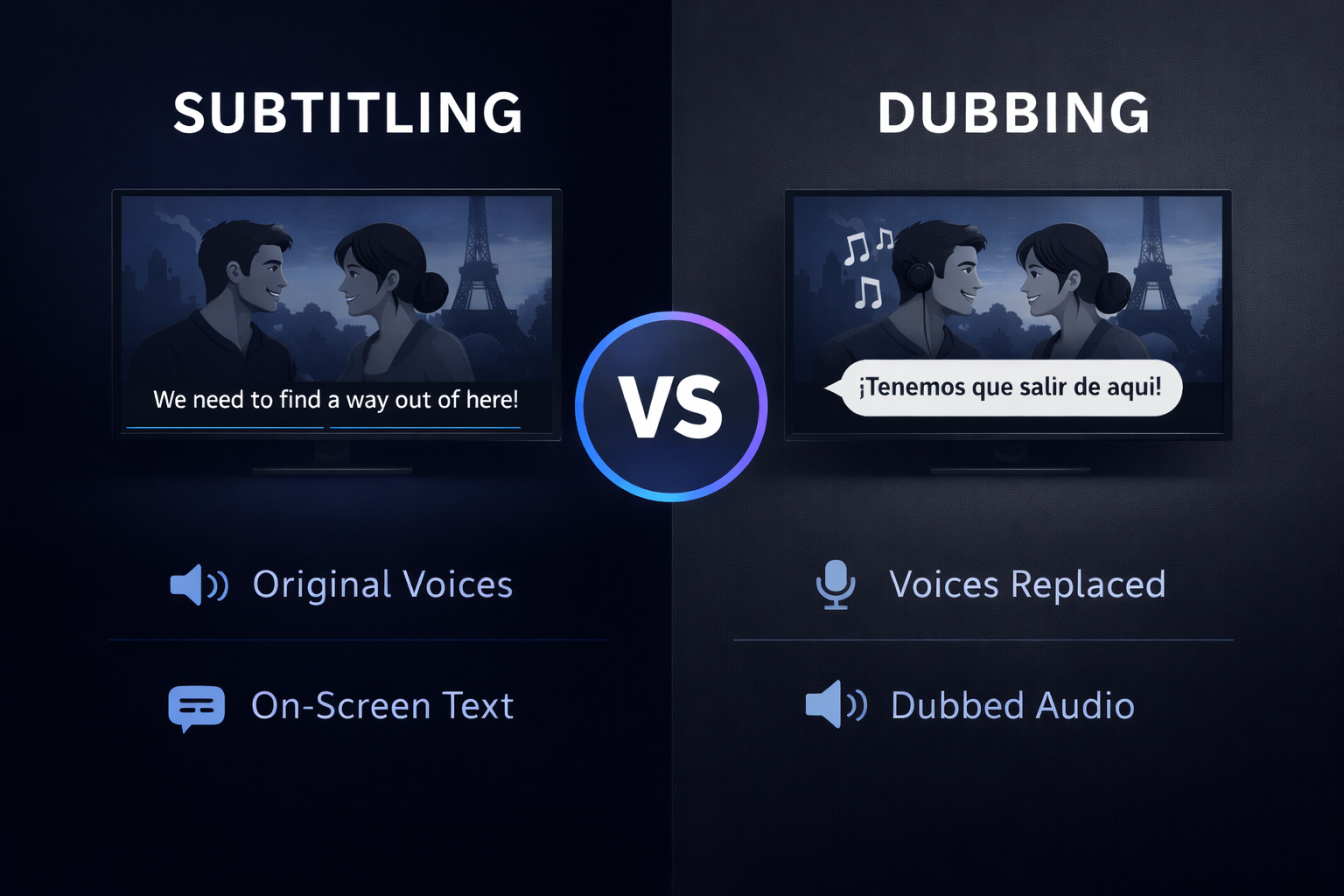
Create AI videos with 240+ avatars in 160+ languages.
Scale cybersecurity training without adding risk
Many cybersecurity incidents begin with situations that feel ordinary or time-sensitive.
An employee receives an email that appears to come from a senior leader, asking them to act quickly. The message looks familiar. Nothing obviously malicious stands out.
Traditional training rarely prepares employees for these moments.
Well-designed cybersecurity training videos do.
In this guide, we’ll explain how to create scalable cybersecurity training videos, including how templates help teams update and localize training without increasing risk or operational overhead.
Cybersecurity training video templates you can customize
Templates make it easier to create cybersecurity training videos that are consistent, reusable, and easy to update as threats change.
Information security training
Use this template to introduce the foundations of information security for non-technical audiences. It works well for:
- Policy overviews and acceptable use guidance
- Everyday behaviors like handling data, devices, and access safely
This template is designed to support clarity and consistency, especially when rolling out baseline security guidance across large or distributed teams.
Cybersecurity training
This template is built around the most common security awareness scenarios organizations train for, including phishing attempts, social engineering, and access misuse.
It’s well suited to:
- Showing realistic email or message scenarios
- Highlighting subtle red flags employees often miss
- Reinforcing exactly what action employees should take when something looks suspicious
Because the structure is repeatable, the same template can be reused across different threats, roles, and regions without losing clarity.
Step 1: Start with a clear learning objective
Begin with a specific situation employees actually face, not a broad security topic.
Instead of “phishing awareness” or “password security,” define scenarios like:
- An email that appears to come from a senior leader requesting urgent action
- A link that looks like a familiar internal tool but isn’t
- A request to bypass a standard approval or access process
Effective cybersecurity training videos focus on moments of decision, because that’s where human-driven risk emerges.
💡Tip: If you want help identifying high-risk moments to train for, see our guide to designing scenario-based training videos.
Step 2: Clarify the decision and expected response
Each video should center on one clear decision the employee needs to make.
Make it explicit:
- What signals indicate potential risk
- What the employee is expected to do in that situation
- Where to report or escalate if something feels off
Avoid listing policies. The goal is to reduce hesitation by reinforcing the correct response in context.
Step 3: Write a short, conversational script
Cybersecurity training videos work best when scripts are:
- Brief and focused
- Written in everyday language
- Addressing the viewer directly
The script should support the visuals, not repeat them. Aim for clarity and recognition rather than completeness.
Step 4: Build the video using scenes and templates
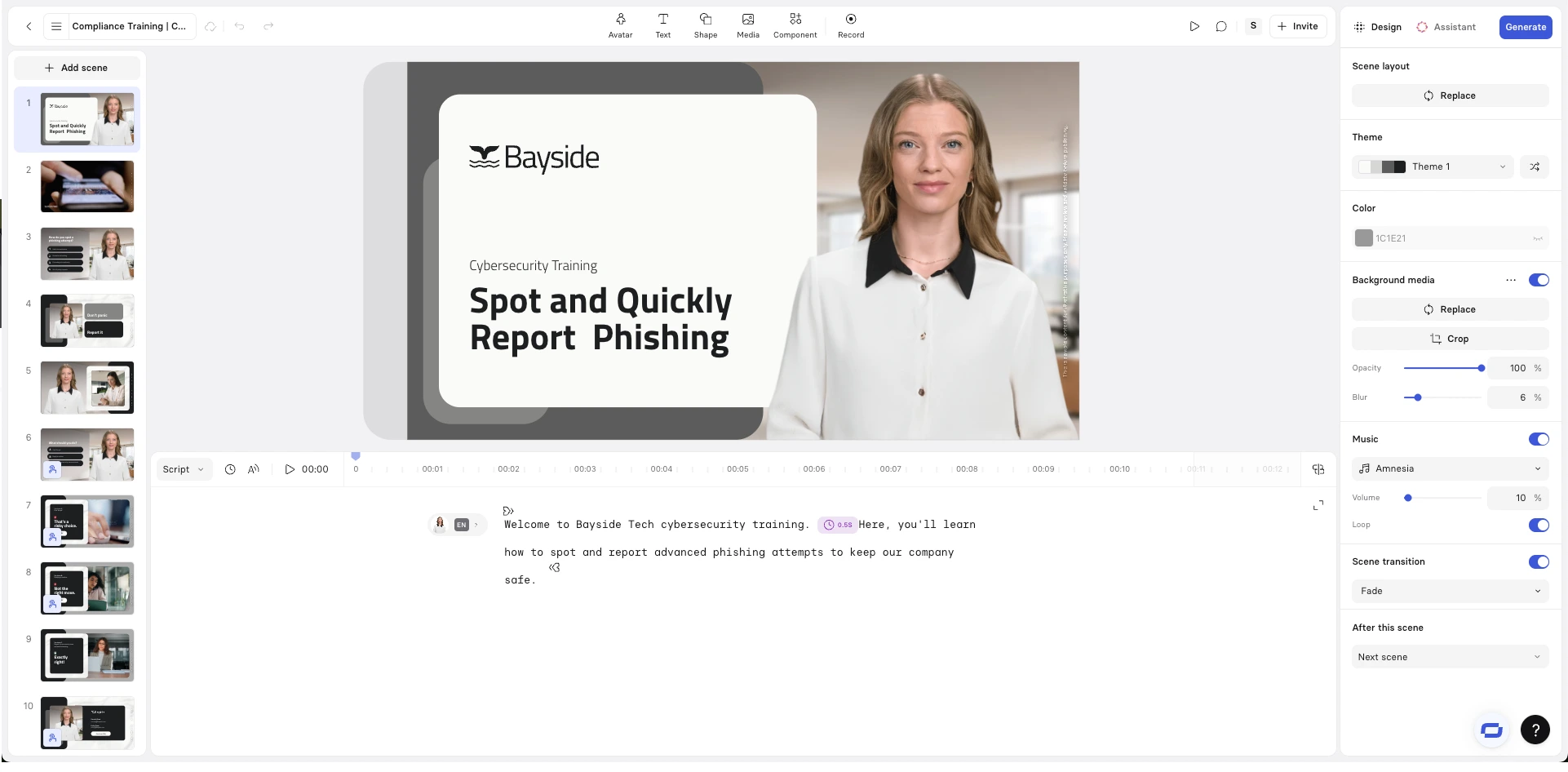
Use scenes and templates to apply a consistent structure across training videos:
- Scenario setup
- Risk signal or decision point
- Expected action
This consistency makes training easier to scale, update, and reuse across roles, regions, and threat types.
💡Tip: Consistent structure matters more than polish. Our FOCA framework explains how to design short, repeatable training videos that scale across teams.
Step 5: Publish, measure, and iterate
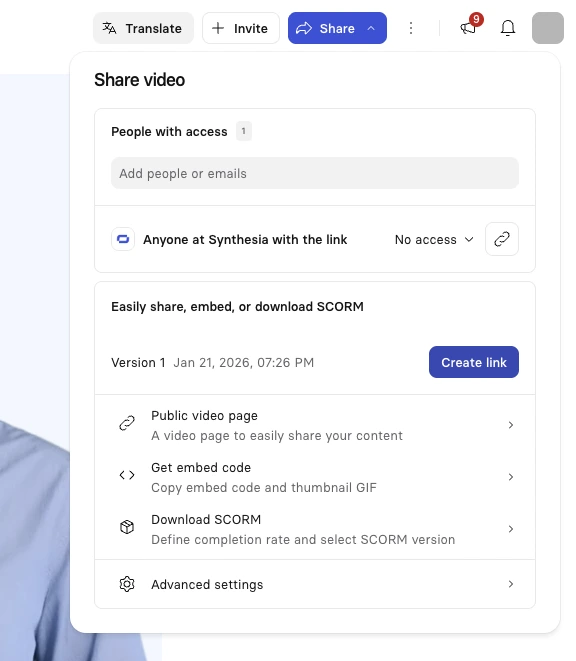
Security awareness training is most effective when it’s treated as an ongoing system.
Design videos so they can be:
- Updated as threat patterns change
- Localized without rewriting everything
- Reused across programs and teams
Short, modular videos make it possible to keep training current without rebuilding entire courses.
In practice, most organizations apply this approach to a small set of scenarios.
Why video works for cybersecurity training
Cybersecurity training succeeds or fails in moments of judgment — when an employee has to recognize risk and decide how to act under pressure. These moments are difficult to prepare for with static policies or text-heavy materials.
Video helps by placing employees inside realistic situations, showing how risk appears in context and what response is expected.
Well-designed cybersecurity training videos:
- Show situations employees are likely to encounter, such as phishing emails or unexpected access requests
- Make consequences visible, so risks aren’t abstract or theoretical
- Clarify the expected action, reducing hesitation in the moment
For non-technical roles especially, this clarity matters. Guidance needs to be concrete and easy to recall when time is limited and context is imperfect.
How to build for scale and consistency
Security awareness training needs to reach everyone — across roles, regions, and levels of technical knowledge — without losing meaning as it scales.
Video supports this by delivering consistent guidance while still allowing teams to adapt visuals, language, and scenarios for different audiences.
Using short videos and reusable templates helps organizations:
- Maintain consistent training across roles and locations
- Reinforce one behavior at a time
- Reuse and combine modules across programs
When security awareness is treated as an ongoing system rather than a one-off course, training is easier to sustain and more likely to influence behavior.
How to build training that stays current
Threats evolve faster than traditional training cycles. When content is difficult to update, it quickly loses credibility.
Modern video workflows make it possible to keep training aligned with real-world risk by:
- Updating specific scenes or guidance without rebuilding entire courses
- Localizing language and examples while preserving the core message
- Rolling out changes quickly as new threats emerge
When training stays current, it remains trustworthy — and employees are more likely to act on it.
Taken together, this research points to a clear design challenge: if cybersecurity training is meant to change behavior, it has to be scenario-based, repeatable, and easy to update.
About the author
Strategic Advisor
Kevin Alster
Kevin Alster is a Strategic Advisor at Synthesia, where he helps global enterprises apply generative AI to improve learning, communication, and organizational performance. His work focuses on translating emerging technology into practical business solutions that scale.He brings over a decade of experience in education, learning design, and media innovation, having developed enterprise programs for organizations such as General Assembly, The School of The New York Times, and Sotheby’s Institute of Art. Kevin combines creative thinking with structured problem-solving to help companies build the capabilities they need to adapt and grow.

What are cybersecurity training videos?
Cybersecurity training videos are short, focused learning assets used to build security awareness and reduce human risk. In enterprise organizations, they support ongoing programs that help employees recognize threats, follow policies, and respond correctly to security incidents.
What is security awareness training?
Security awareness training helps employees understand how their everyday actions affect organizational security. It focuses on behaviors—such as identifying phishing attempts or handling sensitive data—rather than technical cybersecurity skills.
Why are videos effective for cybersecurity training?
Video allows organizations to show realistic scenarios, consequences, and correct actions in context. Compared to text-based training, well-designed videos improve attention, retention, and understanding—especially for non-technical audiences.
How do organizations scale cybersecurity training effectively?
Effective programs break training into short, scenario-based videos, maintain consistent messaging, and update content regularly as threats change. Scalability depends on being able to localize, refresh, and redistribute training without recreating it from scratch.
How often should cybersecurity training videos be updated?
Cybersecurity training should be reviewed regularly and updated whenever threat patterns, tools, or policies change. Many organizations refresh security awareness videos quarterly or alongside audits, incidents, or major regulatory updates.
Can AI video be used for cybersecurity training?
Yes. Many enterprises use AI video to scale cybersecurity training while maintaining consistency. When paired with strong instructional design, AI video supports faster updates, easier localization, and broader reach without increasing production overhead.





.webp)